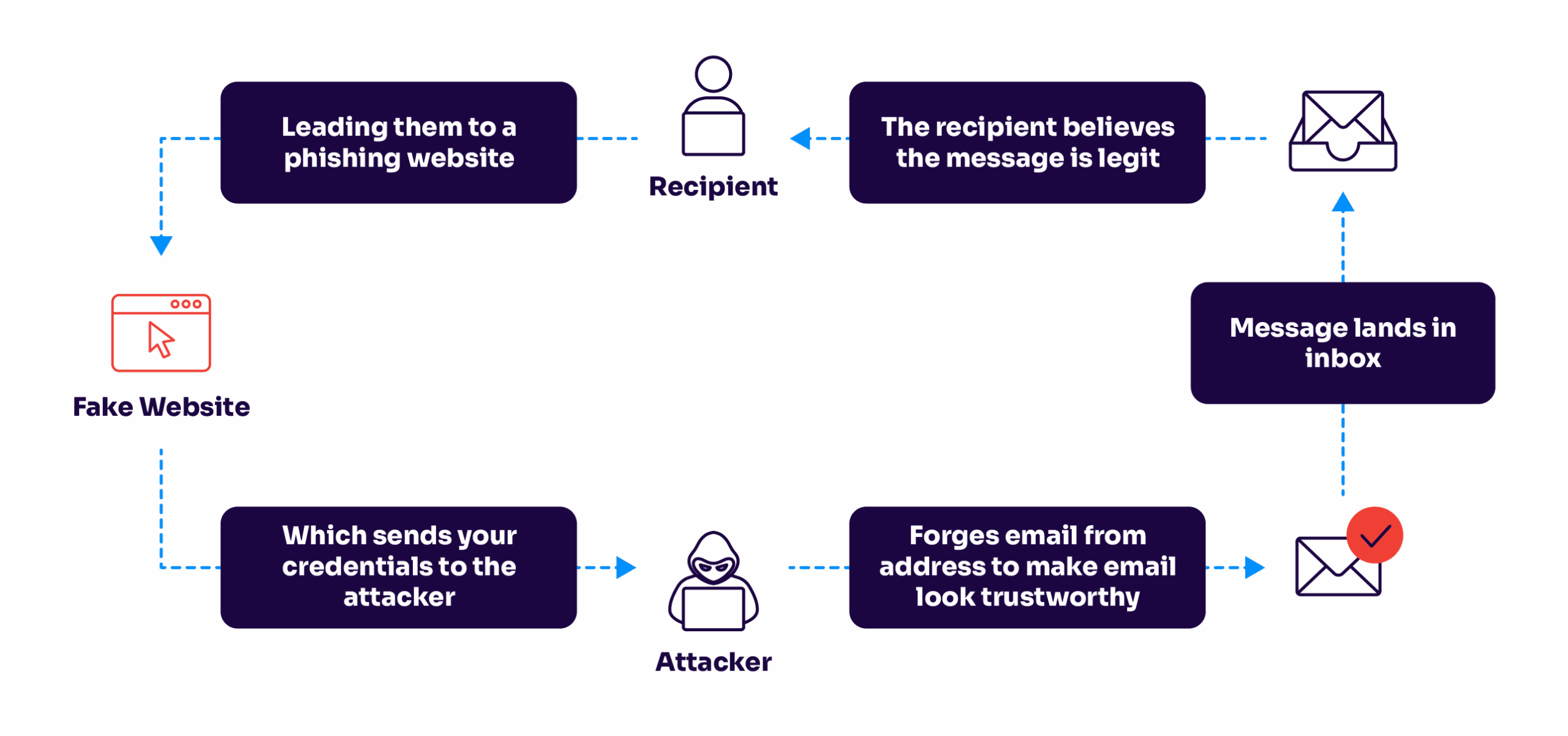
Where It All Began
Earlier today I was stuck trying to analyze shipping data from two warehouses. My usual Excel tricks weren’t cutting it, and my coffee’s getting cold while I’m clicking like a maniac. Then I remembered folks raving about this Joh vs EAC comparison tool on Discord.
First Contact Disaster
Downloaded the installer zip from my buddy’s Google Drive share. Unzipped it, double-clicked the * and BAM! Windows Defender freaked out like I opened a virus piñata. Almost deleted everything right there.
Took me 10 minutes to realize I had to:
- Right-click the installer
- Check “Run anyway” under properties
- Hold my breath while it installed
Making It Actually Work
Opened the ugly gray interface feeling like a caveman discovering fire. Saw two big buttons: Load Joh Data and Load EAC Data. Grabbed my messy CSV files – one from each warehouse system.
First try failed because the dates were formatted differently. Had to:
- Open both CSVs in Notepad
- Change all “/” to “-” in the dates
- Resave as proper comma-separated files
Finally got green checkmarks after reloading. Felt like winning the lottery.
The Magic Button Moment
Clicked Compare Now expecting fireworks. Got spinning wheel hell instead. Thought my potato laptop died. Almost smashed the power button but decided to make more coffee instead. Came back to see this beautiful red/green difference report!
Scrolled through showing mismatched shipments from last month. Turns out Warehouse Joh shorted 17 shipments while EAC had double-billing on 5 orders. No wonder accounting was screaming last week.
Living With My New Superpower
Saved the report as PDF before the tool inevitably crashed (it did). Emailed it to the team with subject line “FOUND THE $$$ LEAK”. Got 3 “YOU ROCK!!” replies before lunch. Now the tool sits on my desktop like a trophy. Still ugly as sin but gets the job done.
Total time invested? About 45 minutes fighting with install + formats. Still better than 3 days of manual checks. Would wrestle Windows Defender again for this.





